Comments
Dumping the Verizon FiOS Actiontec Router
Hoboken is blessed with some decent options when it comes to internet service. Verizon started wiring up most of the town with FiOS back in 2009. This was around the same time that I noticed Cablevision was hitting capacity problems with its distribution nodes, which are the drop points where fiber is converted to coax lines. A recurring symptom of reduced bandwidth in the evening hours hinted at overpopulated (read: oversold) nodes. Rather than wait for Cablevision to upgrade its infrastructure, I jumped over to FiOS as soon as it became available.
Each FiOS installation includes an ONT that converts the fiber-optic cable to coax or Ethernet. Using Ethernet limits you to just internet service, but that’s not a problem at all for cord cutters; however, since my building was already wired for coax and I wasn’t keen on hanging Cat5 cable from my apartment window down to the meter room, I went with coax and Verizon’s bundled Actiontec MI424WR router.
With FiOS, the MI424WR serves double duty as a MoCA bridge, converting coax to usable Ethernet, and router. As far as routers go, it’s not too bad. There’s actually quite a lot of functionality buried behind all of the “Are you sure you want to see the advanced options?” prompts in its admin GUI. The MI424WR’s diminutive NAT table is a common complaint, but I haven’t been affected by it.
Everything was well and good until I stumbled upon my wireless network’s SSID and encryption key on Verizon’s account management page:
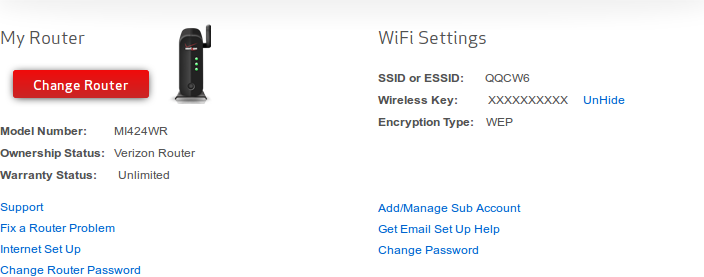
Note: if it wasn’t obvious by the SSID and WEP encryption, I took this screenshot after a router reset.
Clicking “UnHide” did exactly what you might expect: my encryption key was
revealed in plain text. And if you’re curious, the button itself is nothing more
than a bit jQuery that fills in the actual key from a js_passcode variable
defined in the page source. I’m a bit curious if a creative encryption key could
be used to exploit an XSS
vulnerability, but not enough to actually test it out.
It’s obvious that Verizon intended this as some sort of convenience for their customers (likely the type prone to writing their passwords on a post-it note), but this should be a huge red flag for anyone with the slightest concern for privacy and security. I’m not sure when this “feature” was added, and I seldom log in to my account page, but I don’t recall seeing it before.
Of course, I wasn’t the only one that noticed:
When all it takes to reset everything to factory settings for the average brain-dead customer who has forgotten their password or key is to hold the "reset" button for 15 seconds, what possible reasonable justification for this level of intentional security hole is there?
Following the rabbit trail, I came across a lot of discussion about port 4567 and the TR-069 protocol:
- Verizon’s access to the router’s WPA password
- Verizon should not be able to access user private information in routers
- Verizon accessed my router (port 4567, TR-069)
- Verizon changing users’ router passwords
- Port 4567 open on Actiontec router using Verizon FiOS
- Remove the Actiontec Verizon backdoor on port 4567
There was also a captivating tale involving Czech botnets, but that involved a Westell 9100 router, a less-secure predecessor to the modern Actiontec models.
So, Verizon officially uses this to push firmware and security updates. I assume it’s also what they use to pull the router’s SSID and encryption key. At this point, I decided to do what I should have done years ago and replace the Actiontec MI424WR with my own router.
Back when I had a cable modem, I adored my Linksys WRT54G. This is the classic series that lead to DD-WRT, OpenWrt, Tomato, and countless other open-source firmwares. A couple of years ago, Rasmus tweeted about picking up a bunch of WRT160N routers at a great price, so I snap-bought one, flashed it with custom firmware, and set it up as a repeater for my now-insecure wifi network. It did lack the iconic black and blue body of its ancestors, but 802.11n was a welcome upgrade.
Step one of the MI424WR replacement process was heading over to DSLReports’ FiOS FAQ, which is an amazing source of information. I read a few articles about single-purpose MoCa bridges, but apparently not enough, as I ended up purchasing an Actiontec ECB2500 that was completely unsuitable for my use case (thanks, Wei). I found this out only after calling FiOS’ tech support and getting re-routed to some private Actiontec support line intended for Verizon technicians. If you do go this route, you’ll want to (a) read the FAQ in its entirety and (b) pick up either a Netgear MCAB1001 or D-Link DXN-221. These are sold in pairs (unless you can find a DXN-220), so I’d suggest going halfsies with a friend.
After getting rid of the useless Actiontec ECB2500, I was a bit apprehensive about springing for a Netgear or D-Link. Both are increasingly hard to come by, and they don’t come cheap. Thankfully, I found an old thread (from 2007!) in the DSLReports forums with instructions on turning the MI424WR into a MoCa bridge. To paraphrase, the steps are as follows:
- Connect to the MI424WR via Ethernet and perform a factory reset from the Advanced section of the admin GUI.
- Log back in to the router using the default “admin” and “password” credentials, and access Network Connections under My Network.
- Access the settings for Broadband Connection (Coax) and ensure the privacy option is selected. Release the MI424WR’s IP address and immediately change the Internet Protocol option to “No IP address” to prevent a new IP from being requested.
- Access the settings for Network (Home/Office) and enable Broadband Connection (Coax) under the list of bridged connections. The original guide referred to a STP checkbox, but I never saw it listed for the coax connection.
- Disable the Wireless Access Point network interface completely and remove it from any bridge configuration.
- If necessary, change the Firewall Settings to the minimum setting.
- At this point, the main page of the admin GUI should complain that it has no internet connection, but Broadband Connection (Coax) should still show up as “connected” in the list of network interfaces.
- Configure your preferred router with an IP address other than 192.168.1.1 and connect its WAN port to the MI424WR’s LAN port. The router should then be able to pick up a new Verizon IP address via DHCP.
Once the MI424WR is in bridge mode, its admin GUI will be inaccessible unless you connect directly to one of its LAN ports with a static IP address in the same subnet. As an added benefit, open port 4567 should no longer be an issue. For FiOS TV customers with a set-top box, the original thread I referenced has since been superseded with a new guide, which includes additional instructions for ensuring compatibility with VOD services.

When the bridge up and running, there was just one more thing to fix. My MI424WR had been configured so long ago that I completely forgot about Verizon’s dreadful DNS servers, which like to resolve non-existent domains to search.dnsassist.verizon.net and conveniently load up a page full of Yahoo search results and targeted ads. Thankfully, I can rely on Google’s DNS servers to behave properly.